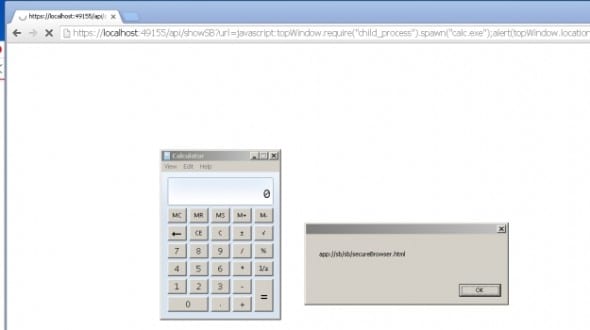
Trend Micro’s Password Manager. It is strange to believe that an extension that protects user’s sensitive credentials would be the one with a vulnerability but even the most secure platforms often have an opening that can be found out with relative ease. With the latest vulnerability, an attacker can remotely execute arbitrary code and you will clearly be able to see from the screenshot that all it took was a bit of specially-crafted JavaScript. However, if you try to look for the Password Manager in the Chrome Web Store, you will not be able to stumble upon it. That is because it is delivered during the installation of their Windows antivirus software or as a standalone application. If you had accidentally or purposely hooked it to your Google Chrome, your browser would eventually be exposing 70 of its APIs to the World Wide Web. Thankfully, the vulnerability was not effectively or actively exploited and the original issue has been fixed completely, at least according to the reports. Unfortunately, another report states that it is quite easy to bypass the security extension, and something as small as a PDF containing Trojan-like properties will easily be able to do the trick. Sadly, Trend was not the only company that the tech giant Google has called out. Engineers just got finished resolving a similar issue with AVG over their Web TuneUp extension and we should be commending on these employees who go out of their way to seal a vulnerability before a malicious hackers finds out about it.